What happened?
Today we discovered that a mail account hosted on our cloud service was abused for sending spam. Some evil person gained access to the account and sent thousands of horrible mails into the world.
How we took action
After cleaning up the mess and changing the password of the affected account I thought about prevention in the future.
Until today, when you created a mailbox in Group-Office you enabled this account for receiving but also for sending
mail via this username. This is not required when you only use the Group-Office web mail interface or connect
a phone via ActiveSync. Then you authenticate with your Group-Office account and it can send mail on the local
net without a password. So for 90% of the users
it's not required to connect via SMTP from outside the network. Only when you setup a desktop client this is needed.
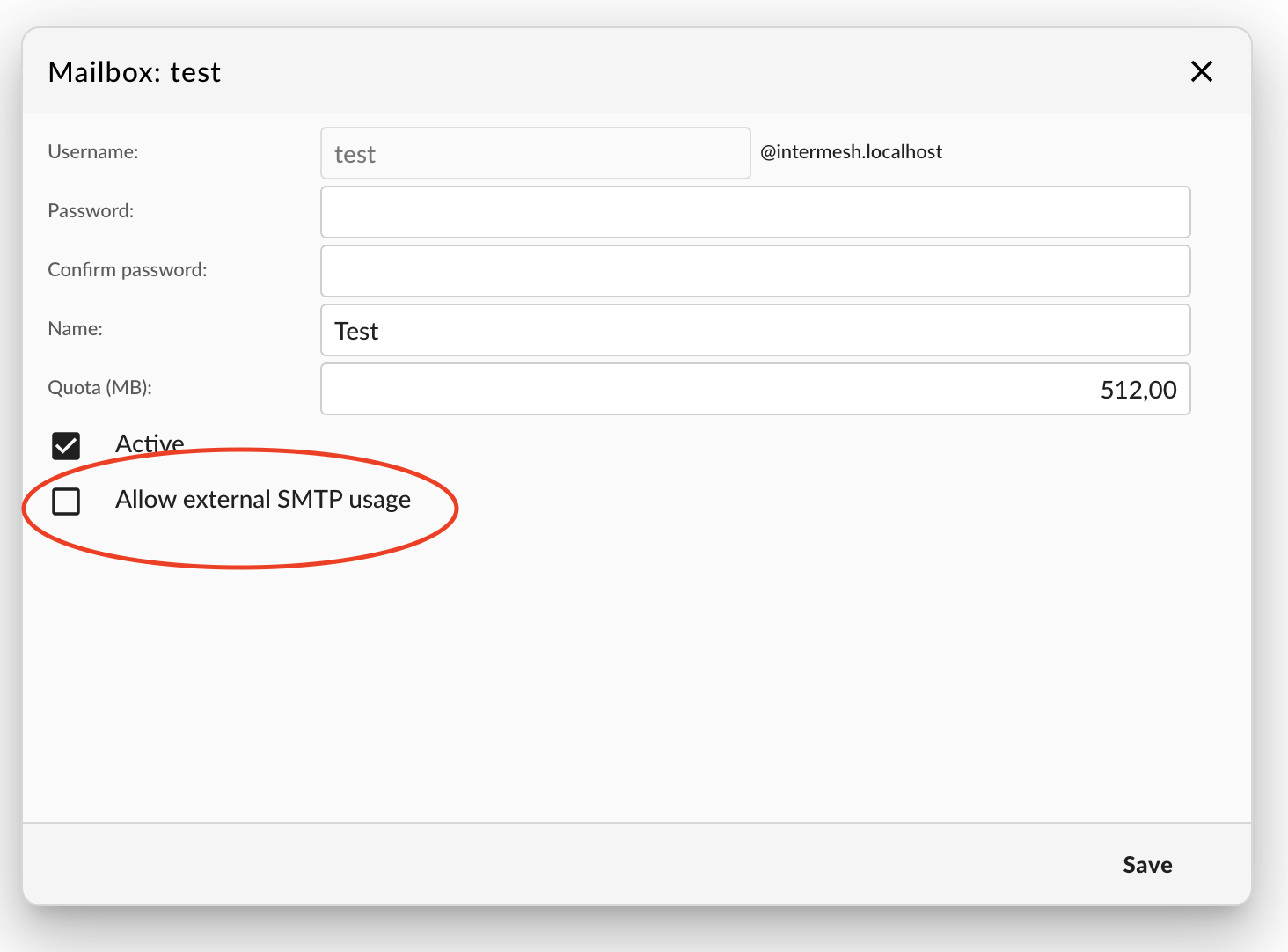
So we decided to implement a new checkbox to allow outside SMTP access which is disabled by default.
Upgrading
Keep this new security feature in mind when you upgrade to Group-Office 6.6.137 if you use the
Group-Office mailserver too.
We scanned the mail logs for accounts logging in and enabled access for those who depend on it before applying this update.
I hope we made the world a bit safer with this measure!